Proximus, which formerly known as Belgacom, is a Belgian telecommunications company which offers fixed line solutions and mobile communications solutions
The XSS-itself:
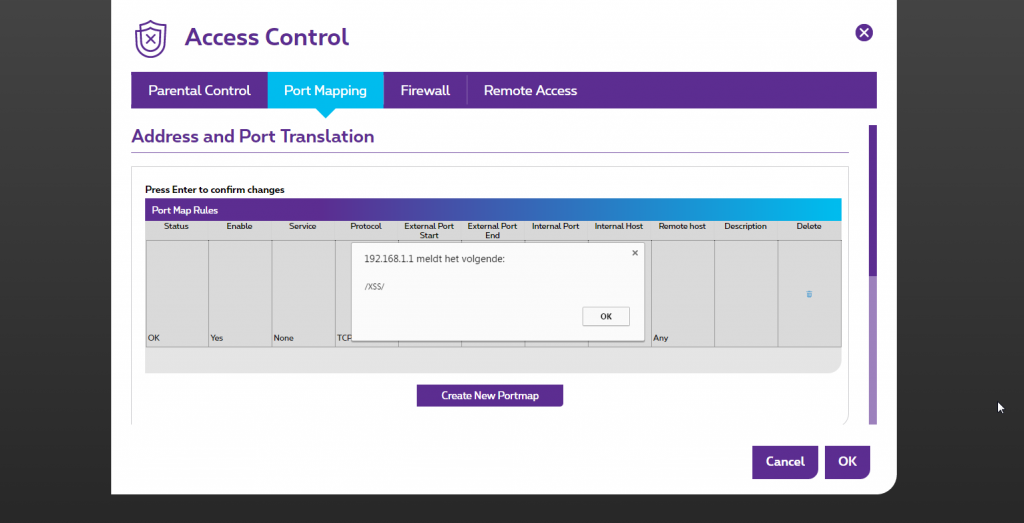
You could insert a malicious script as a description in a new port map; this wasn’t filtered or validated by the system. If the user loads the port mapping option or port mapping tab, the XSS will activate.
Steps to produce this XSS:
1. Login as user on 192.168.1.1 (router interface bbox3)
2. Select access control tab
3. Port mapping tab
4. Create new port map
5. Enter the following in the description form: <iframe src=”http://www.triponoid.com ” onmouseover=alert(/XSS/)></iframe>
6. Enter some random data in the other fields
Extra info:
*Authentication Required
You can still use this script to try it out yourself, but they have fixed the problem, and the script will not be stored in the datafields anymore.
Resolved
Quick response from the Proximus team on Twitter, they’ve immediately fixed this.

Leave a Reply